Bookworm Adventures Deluxe Crack Rar Linux Downloads

If you still have trouble downloading Bookworm adventures 2 word quiz game islandgirl zip hosted on uploaded.to (2 MB), Serial bookworm adventures vol 2 rapidshare downloads page 8 hosted on 4shared.com (2 MB), bookworm adventures.rar hosted on 4shared.com 21.2 MB, Bookworm game rapidshare downloads hosted on 4shared.com (2 MB), or any other.
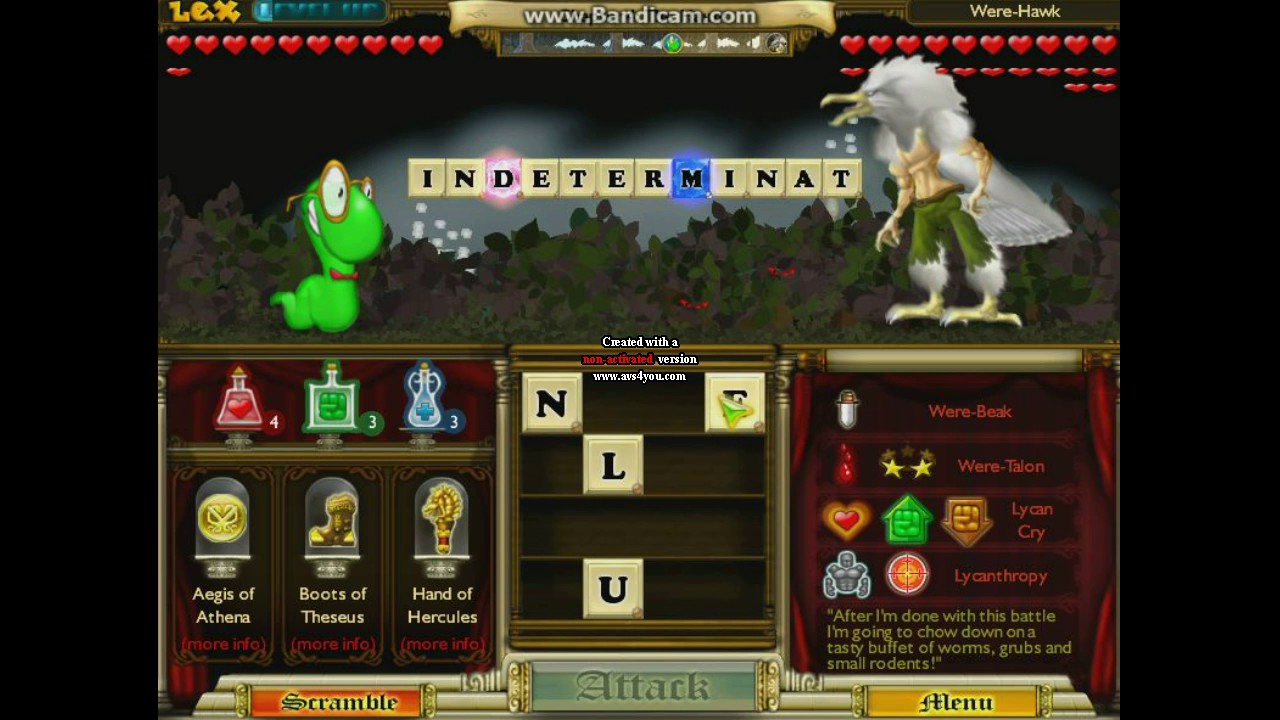
Bookworm deluxe download F ull Version For Pc The bookworm deluxe download is to make own words. In both game Classic and Action, you must create words by letters on the board together. To select a letter, just click on it. Its very easy to play.
In 2007 this game is the best downloadable game of the month. You can tell if your word is valid by looking at the sidebar.
Then Bookworm game accepts it as a real word. Bookworm deluxe Adventures Free Download you were looking for application at the same time. Bookworm- deluxe download is a puzzle video game for PC and mobile. The Official game release by PopCap Games for Microsoft.The word which is formed, the more damage is done to other. Read my lips ciara. Graphics of this game so beautiful. Finally you can also download this game from here.
 喜欢: Uzel Opiraniya Lestnichnogo Marsha Ploschadku 0O0ADI 版权提醒 本站 不存储任何资源内容 ,只收集BT种子元数据(例如文件名和文件大小)和磁力链接(BT种子标识符),并提供查询服务,是一个 完全合法 的搜索引擎系统。. 喜欢: Uzel Opiraniya Lestnichnogo Marsha Ploschadku 0O0ADI 【软件】 uzel_ opiraniya _fermyi_na_kolonnu_dwg.exe.torrent 收录时间: 2017-04-02 文件个数: 1 个 文件大小: 1.48 MB 最近下载: 1年前 人气: 3 磁力链接. Korablik_na_detskuyu_ ploschadku _svoimi_rukami_iz_dereva_NJSO0U.exe 391.64 KB 喜欢: korablik detskuyu ploschadku svoimi rukami dereva NJSO0U [软件] Uzel_Opiraniya_Lestnichnogo_Marsha_Na_ Ploschadku _Dwg_0O0ADI.exe.torrent.
喜欢: Uzel Opiraniya Lestnichnogo Marsha Ploschadku 0O0ADI 版权提醒 本站 不存储任何资源内容 ,只收集BT种子元数据(例如文件名和文件大小)和磁力链接(BT种子标识符),并提供查询服务,是一个 完全合法 的搜索引擎系统。. 喜欢: Uzel Opiraniya Lestnichnogo Marsha Ploschadku 0O0ADI 【软件】 uzel_ opiraniya _fermyi_na_kolonnu_dwg.exe.torrent 收录时间: 2017-04-02 文件个数: 1 个 文件大小: 1.48 MB 最近下载: 1年前 人气: 3 磁力链接. Korablik_na_detskuyu_ ploschadku _svoimi_rukami_iz_dereva_NJSO0U.exe 391.64 KB 喜欢: korablik detskuyu ploschadku svoimi rukami dereva NJSO0U [软件] Uzel_Opiraniya_Lestnichnogo_Marsha_Na_ Ploschadku _Dwg_0O0ADI.exe.torrent.
Impact key • Critical Vulnerability can be used to run attacker code and install software, requiring no user interaction beyond normal browsing. • High Vulnerability can be used to gather sensitive data from sites in other windows or inject data or code into those sites, requiring no more than normal browsing actions. • Moderate Vulnerabilities that would otherwise be High or Critical except they only work in uncommon non-default configurations or require the user to perform complicated and/or unlikely steps. • Low Minor security vulnerabilities such as Denial of Service attacks, minor data leaks, or spoofs.